|  |
| Home | Solutions/Products | Deployment/Installation | About Cryptography | User Manual | Tutorial | FAQ |
|
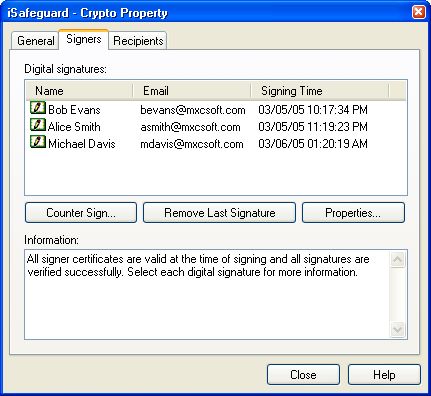
CountersignaturesCountersignature is one of the most important applications of public key cryptography. In this section we will introduce countersignature. What is a countersignature?A countersignature is a signature of an existing signature and message or a signature of an existing signature. Why are countersignatures important?Countersignatures are important when, for example, a lawyer prepares and digitally signs a legal document and then sends to his client, expecting the client to confirm agreement with the terms contained in the document. The client reads the terms and, if in agreement, countersigns the document. The countersigned document is then sent back to the lawyer. The lawyer now knows, and can prove, that the client agreed to the terms. How countersignatures are generated?A countersignature is generated by signing the encrypted hash of an existing signature. It is possible to countersign a countersignature when more than two people need to agree on the terms of a document. The following screen shot shows the signature and countersignatures of a signed and encrypted document.
In the above example Bob (the first signer) calculates the hash (or digest) of the data and then signs (encrypts with the his private key) the hash value to generate a signature. Alice (the first counter signer) countersigns the signature of the first signer, Bob. Michael (the second counter signer) countersigns Alice's countersignature; and so on and so forth. A chain of signature and countersignatures are created. From the above process you can see the order of the signature and countersignatures is important and reserved. Conforming to standardsThe digital signature and countersignatures generated by iSafeguard™ conform to PKCS #7 and PKCS #9. For more information about digital signatures and countersignatures please contact us at help@mxcsoft.cm or refer to PKCS #7 and PKCS #9 references at RSA web site http://www.rsa.com. Signing and countersigning are complex processes. However when using iSafeguard™ you will find it very easy to sign and countersign your important documents of any types and your emails. | |||||||||||||||||||||||||||||||||||||||||
| Trademarks | Copyright ?2001-2007 MXC Software. All rights reserved. |